Software as a Service (SaaS) has revolutionized the world of business technology. As a model of cloud computing, it provides businesses access to software applications over the Internet without the need for in-house infrastructure or hardware. SaaS applications run directly through a web browser, eliminating the need for downloads or installations, and are typically paid for through a subscription model. As the SaaS industry continues to evolve, it’s accompanied by a unique set of key SaaS terms, jargon, and phrases, which are crucial to understanding for anyone navigating this space.
These Key SaaS terms not only enable one to comprehend the technical aspects of SaaS but also facilitate better decision-making in terms of investments, strategies, and utilization of SaaS solutions.
From fundamental terminologies like API, Churn Rate, and Customer Acquisition Cost (CAC), to more complex ones like Multi-Tenancy and Machine Learning, the world of SaaS is rich with specific terms that shape the understanding and application of these cloud-based services. Before moving the list of key SaaS terms let’s first understand the importance and benefits of knowing this SaaS terminology.
Importance and Benefits of Understanding ” Key SaaS Terms’ :
Understanding Key SaaS terms is a fundamental requirement for anyone aiming to leverage the power of cloud-based services effectively. Whether you’re a business owner, a tech professional, or someone simply interested in the field, being familiar with these terms will prove invaluable. Here’s why:
1. Improved Decision-Making:
A solid understanding of SaaS terms can help business leaders make informed decisions about the tools and services that are most suitable for their organization. When you can distinguish between terms like multi-tenancy, scalability, and integration, you’re better equipped to evaluate different SaaS options and choose the ones that align with your business needs.
2. Enhanced Communication:
The language of SaaS is widely used in the tech industry. Familiarity with these terms can facilitate clearer communication with service providers, developers, IT staff, and even within your team. It can help avoid misunderstandings and ensure that everyone is on the same page regarding the expectations and functionality of your SaaS applications.
3. Better Utilization of Services:
Understanding SaaS terms can also help you to fully utilize the features and benefits offered by your SaaS applications. Knowing what terms like API, data syncing, or real-time messaging mean. Can help you leverage these features for the benefit of your business.
4. Future-Proofing Your Business:
As businesses continue to shift towards digital solutions, knowledge of SaaS and related terms becomes increasingly crucial. A strong understanding of these terms will keep you ahead of the curve. And enabling you to adapt as new technologies and services become available quickly.
5. Problem-Solving and Troubleshooting:
If an issue arises with a SaaS application, understanding SaaS jargon will help you better comprehend the problem and communicate it effectively with support services. This can lead to quicker resolution of problems, minimizing downtime and disruption.
6. Increased Confidence:
Lastly, understanding key SaaS terms can increase your confidence when engaging with SaaS providers or discussing SaaS solutions within your organization. This knowledge can empower you to ask the right questions, understand the provided answers, and ultimately make the best decisions for your business. Here is a list of highly important SaaS terminology that you need to know.
List Of Highly Important SaaS Terminology (Key SaaS Terms)
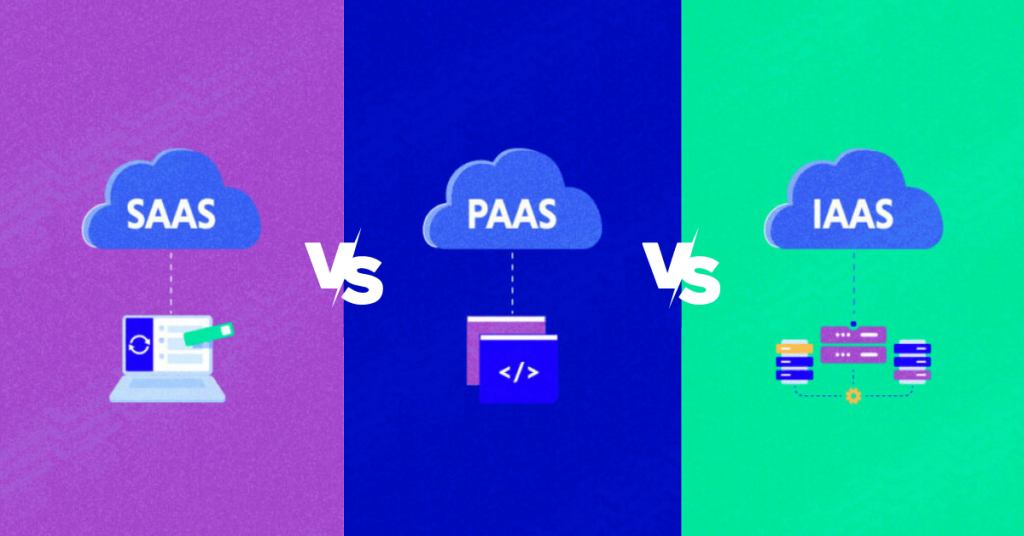
1. SaaS: Software as a Service.
A software distribution model where applications are hosted by a service provider and made available to customers over the Internet.
2. PaaS: Platform as a Service.
A category of cloud computing that provides a platform for customers to develop, run, and manage applications without the complexity of building and maintaining the infrastructure.
3. IaaS: Infrastructure as a Service.
A type of cloud computing that provides virtualized computing resources over the internet.
To know the difference between SaaS vs PaaS vs IaaS in detail Click Here.
4. Cloud Computing:
The delivery of computing services over the internet (‘the cloud’) rather than on local servers or personal devices.
5. API: Application Programming Interface.
A set of rules and protocols for building and interacting with software applications.
6. On-Premises Software:
Software installed and runs on computers on the premises of the person or organization using the software, rather than at a remote facility, such as a server farm or cloud.
7. Subscription Model:
A business model where a customer pays a recurring price at regular intervals for access to a product or service.
8. Multi-tenancy:
A principle in software architecture where a single instance of the software runs on a server, serving multiple tenants (users).
9. SLA: Service Level Agreement.
A contract between a service provider and the end user defines the level of service expected from the service provider.
10. Uptime:
The time a system or service is up and operational.
11. Downtime:
The time a system or service is not operational or unavailable.
12. Churn Rate:
The rate at which customers stop doing business with an entity over a given period of time.
13. ARR: Annual Recurring Revenue.
The value of the contracted recurring revenue components of your term subscriptions normalized to a one-year period.
14. MRR: Monthly Recurring Revenue.
The amount of revenue a subscription-based business receives per month.
15. CAC: Customer Acquisition Cost.
The cost associated with convincing a customer to buy a product/service.
16. LTV: Lifetime Value.
A prediction of the net profit attributed to the entire future relationship with a customer.
17. Freemium:
A business model, especially on the Internet, whereby basic services are provided free of charge while more advanced features must be paid for.
18. User Interface (UI):
The space where interactions between humans and machines occur.
19. User Experience (UX):
A person’s emotions and attitudes about using a particular product, system or service.
20. CRM: Customer Relationship Management.
A strategy for managing an organization’s relationships and interactions with customers and potential customers.
21. ERP: Enterprise Resource Planning.
A business process management software that allows an organization to use a system of integrated applications to manage the business and automate many back office functions related to technology, services and human resources.
22. Data Migration:
The process of transferring data between data storage systems, data formats or computer systems.
23. Data Integration:
The process of combining data from different sources into a single, unified view.
24. Webhook:
A method of augmenting or altering the behaviour of a web page or web application with custom callbacks.
25. OAuth:
An open standard for access delegation, commonly used as a way for Internet users to grant websites or applications access to their information on other websites but without giving them the passwords.
26. Single Sign-On (SSO):
A property of access control of multiple related, yet independent, software systems, where a user logs in once and gains access to all systems without being prompted to log in again.
27. Multi-Tenancy:
A software architecture in which a single instance of software runs on a server and serves multiple tenants (customers). In a multi-tenant architecture, each tenant’s data is isolated and remains invisible to other tenants.
28. Microservices:
An architectural style that structures an application as a collection of services that are highly maintainable and testable, loosely coupled, independently deployable, and organized around business capabilities.
29. Agile Methodology:
A type of project management process, mainly used for software development, where demands and solutions evolve through the collaborative effort of self-organizing and cross-functional teams.
30. Scalability:
The capability of a system, network, or process to handle a growing amount of work, or its potential to be enlarged to accommodate that growth.
31. Vertical Scaling:
Adding more resources such as processing power or memory to a server, or replacing one server with a more powerful one.
32. Horizontal Scaling:
Adding more machines to a network to improve performance and the ability to manage a high level of requests.
33. Serverless Architecture:
A software design pattern where applications are hosted by a third-party service, eliminating the need for server software and hardware management by the developer.
34. Data Encryption:
The method of using an algorithm to transform data into a form that is unreadable without a decryption key. Used to protect sensitive information.
35. Data Decryption:
The process of decoding data that has been encrypted into a secret format.
36. Two-Factor Authentication (2FA):
A security process in which the user provides two different authentication factors to verify themselves.
37. Load Balancing:
The practice of distributing network traffic across multiple servers to ensure no single server bears too much demand.
38. Data Center:
A large group of networked computer servers typically used by organizations for the remote storage, processing, or distribution of large amounts of data.
39. Database:
An organized collection of data, generally stored and accessed electronically from a computer system.
40. Data Breach:
An incident where information is stolen or taken from a system without the knowledge or authorization of the system’s owner.
41. Firewall:
A network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules.
42. Intrusion Detection System (IDS):
A system that monitors a network or systems for malicious activity or policy violations.
43. Intrusion Prevention System (IPS):
A system that examines network traffic flows to detect and prevent vulnerability exploits.
44. Malware:
Software that is specifically designed to disrupt, damage, or gain unauthorized access to a computer system.
45. Phishing:
The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
46. Ransomware:
A type of malicious software designed to block access to a computer system until a sum of money is paid.
47. Virtual Private Network (VPN):
A network that is constructed using public wires to connect nodes and that uses encryption to secure data.
48. Data Loss Prevention (DLP):
A set of tools and processes used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users.
49. Backup:
The process of creating a copy of data and storing it so it may be restored in the event of data loss.
50. Disaster Recovery:
A set of policies and procedures to enable the recovery or continuation of vital technology infrastructure and systems following a natural or human-induced disaster.
51. Business Continuity Plan (BCP):
The process involved in creating a system of prevention and recovery from potential threats to a company.
52. BYOD (Bring Your Own Device):
A policy allowing employees to bring their own personal devices to their workplace, and to use those devices to access privileged company information and applications.
53. Sandbox:
A testing environment that isolates untested changes and outright experimentation from the production environment or repository.
54. Software Development Kit (SDK):
A set of software development tools that allows the creation of applications for a certain software package, software framework, hardware platform, computer system, video game console, operating system, or similar development platform.
55. DevOps:
A set of practices that combines software development and IT operations with the aim to shorten the systems development life cycle and provide continuous delivery with high software quality.
56. Continuous Integration (CI):
The practice of merging all developers’ working copies to a shared mainline several times a day.
57. Continuous Deployment (CD):
A software engineering approach in which software functionalities are delivered frequently through automated deployments.
58. Version Control:
A system that records changes to a file or set of files over time so that you can recall specific versions later.
59. Git:
A distributed version control system for tracking changes in source code during software development.
60. GitHub:
A web-based hosting service for version control using Git, plus its own features.
61. Docker:
An open-source platform used for developing, shipping, and running applications inside lightweight, portable containers.
62. Containerization:
A lightweight alternative to full machine virtualization that involves encapsulating an application in a container with its own operating system.
63. Kubernetes:
An open-source platform designed to automate deploying, scaling, and operating application containers.
64. Microservices Architecture:
A variant of the service-oriented architecture (SOA) architectural style that structures an application as a collection of loosely coupled services.
65. Artificial Intelligence (AI):
The theory and development of computer systems able to perform tasks that normally require human intelligence.
66. Machine Learning:
A type of artificial intelligence that provides computers with the ability to learn without being explicitly programmed.
67. Deep Learning:
A subfield of machine learning concerned with algorithms inspired by the structure and function of the brain called artificial neural networks.
68. Natural Language Processing (NLP):
A subfield of linguistics, computer science, and artificial intelligence concerned with the interactions between computers and human language.
69. Chatbot:
A computer program that simulates and processes human conversation, allowing humans to interact with digital devices as if they were communicating with a real person.
70. Predictive Analytics:
The use of data, statistical algorithms and machine learning techniques to identify the likelihood of future outcomes based on historical data.
71. Big Data:
Extremely large data sets that may be analyzed computationally to reveal patterns, trends, and associations, especially relating to human behavior and interactions.
72. Data Mining:
The practice of examining large databases in order to generate new information.
73. Data Warehousing:
A large store of data accumulated from a wide range of sources within a company and used to guide management decisions.
74. Business Intelligence (BI):
Strategies and technologies used by enterprises for the data analysis of business information.
75. ETL:
Extract, Transform, Load. A process in database usage, especially in data warehousing.
76. Data Lake:
A storage repository that holds a vast amount of raw data in its native format until it is needed.
77. NoSQL Database:
A non-relational database that provides a mechanism for storage and retrieval of data that is modeled in means other than the tabular relations used in relational databases.
78. SQL Database:
A relational database, which uses Structured Query Language (SQL) to define and manipulate the data.
79. Data Science:
An interdisciplinary field that uses scientific methods, processes, algorithms and systems to extract knowledge and insights
80. Data Visualization:
The graphic representation of data, used to see and understand patterns, outliers, and trends in data.
81. Business Analytics (BA):
The practice of iterative, methodical exploration of an organization’s data, with an emphasis on statistical analysis.
82. Dashboard:
A graphical representation of data that provides visual feedback on the performance of a business, a specific process, or a department.
83. Key Performance Indicator (KPI):
A measurable value that demonstrates how effectively a company is achieving key business objectives.
84. Return on Investment (ROI):
A performance measure used to evaluate the efficiency of an investment or to compare the efficiency of a number of different investments.
85. Total Cost of Ownership (TCO):
A financial estimate intended to help buyers and owners determine the direct and indirect costs of a product or system.
86. Customer Success:
The business methodology of ensuring customers achieve their desired outcomes while using your product or service.
87. Customer Support:
A range of customer services to assist customers in making cost-effective and correct use of a product.
88. Help Desk:
A resource intended to provide the customer or end user with information and support related to a company’s or institution’s products and services.
89. Ticketing System:
A management tool that processes and catalogs customer service requests.
90. Knowledge Base:
A technology used to store complex structured and unstructured information used by a computer system.
91. Self-Service Portal:
A website, part of a company’s service offering, that enables customers to service their own needs.
92. Customer Satisfaction Score (CSAT):
A metric used in the field of customer service to measure the degree to which a product or a service meets or surpasses customer expectation.
93. Net Promoter Score (NPS):
A measure of how likely customers are to recommend a company, product or service to a friend or colleague.
94. Customer Effort Score (CES):
A type of customer satisfaction survey metric that measures the ease of an experience with a company.
95. Average Handle Time (AHT):
A call center metric for the average duration of one transaction, typically measured from the customer’s initiation of the call and including any hold time, talk time and related tasks.
96. First Call Resolution (FCR):
An important metric in customer support that measures the percentage of calls resolved by the support team on the first interaction with the customer.
97. Service Level Objective (SLO):
A key element of a service level agreement (SLA) between a service provider and a customer. SLOs are agreed as a means of measuring the performance of the Service Provider.
98. Integration:
The process of combining different subsystems or components as parts of a larger system.
99. Web Services:
Software system designed to support interoperable machine-to-machine interaction over a network.
100. REST API (Representational State Transfer API):
A set of conventions for designing networked applications.
101. SOAP (Simple Object Access Protocol):
A messaging protocol specification for exchanging structured information in the implementation of web services in computer networks.
102. GraphQL:
A data query and manipulation language for APIs, and a runtime for executing those queries with your existing data.
103. JSON (JavaScript Object Notation):
A lightweight data-interchange format that is easy for humans to read and write and easy for machines to parse and generate.
104. XML (eXtensible Markup Language):
A software and hardware independent tool for storing and transporting data.
105. CSV (Comma Separated Values):
A simple file format used to store tabular data, such as
106. Low-Code/No-Code Platforms:
Software that provides an environment programmers use to create application software through graphical user interfaces and configuration instead of traditional computer programming.
107. Progressive Web Apps (PWAs):
A type of application software delivered through the web, built using common web technologies including HTML, CSS and JavaScript.
108. Single-Page Application (SPA):
A web application or website that interacts with the user by dynamically rewriting the current web page with new data from the web server, instead of the default method of the browser loading entire new pages.
109. Responsive Web Design:
An approach to web design that makes web pages render well on a variety of devices and window or screen sizes.
110. Push Notification:
A message that pops up on a mobile device or desktop. App publishers can send them at any time; users don’t have to be in the app or using their devices to receive them.
111. Real-Time Messaging:
A method of communication which is live and instantaneous, often seen in chat interfaces.
112. Data Sync (Synchronization):
The process of establishing consistency among systems and subsequent continuous updates to maintain consistency.
113. WebRTC (Web Real-Time Communication):
An open-source project providing web browsers and mobile applications with real-time communication via simple application programming interfaces.
114. IPaaS (Integration Platform as a Service):
A set of automated tools for connecting software applications that are deployed in different environments. IPaaS is often used by large business-to-business (B2B) enterprises that need to integrate on-premises applications and data with cloud applications and data.
115. Auto-scaling:
The process by which a cloud system automatically adds or removes resources depending upon the actual usage.
116. Latency:
The delay before a transfer of data begins following an instruction for its transfer.
117. Bandwidth:
The maximum rate of data transfer across a given path.
118. Data Compression:
The process of reducing the size of a data file.
119. Edge Computing:
A distributed computing paradigm that brings computation and data storage closer to the location where it is needed, to improve response times and save bandwidth.
120. Fog Computing:
A decentralized computing infrastructure in which data, computing, storage and applications are distributed in the most logical, efficient place between the data source and the cloud.
Conclusion – Key SaaS Terms
Understanding Key SaaS terms is not just a matter of expanding your vocabulary. It’s about improving your ability to navigate the digital world, making more strategic decisions, and harnessing the full power of the cloud for your business. Also, Stay up-to-date with the key SaaS terms and trends to stay ahead of the competition and make the most out of your technology investments.